Applications and Security Protocols
The Thumbpod has a number of application areas, including secure wireless pay-point transactions, high-throughput encrypted streaming, and universal key functionality. A current application that has been developed is the wireless pay-point protocol with biometric authentication.Biometric Authentication Protocol
We have developed a wireless pay-point protocol for financial transactions using the ThumbPod embedded system. The protocol is unique in that no sensitive biometric data is sent over a secure or insecure channel and all biometric signal processing functionality is localized in the ThumbPod. The protocol allows for mutual authentication between the ThumbPod and the server and authenticates a strong tie between the user and ThumbPod. We have also developed a novel generation function utilizing fingerprint biometrics and dynamic cryptographic components.Design Flow-Hardware/Software Acceleration Transparency
The entire protocol has been simulated as a Java application on a workstation and is being migrated onto a HW/SW embedded environment based on an FPGA board. The embedded environment not only emulates the original application but performs selective software and hardware acceleration to performance-critical functions using a methodology we developed called "hardware/software acceleration transparency." The various abstraction levels can be seen on the figure.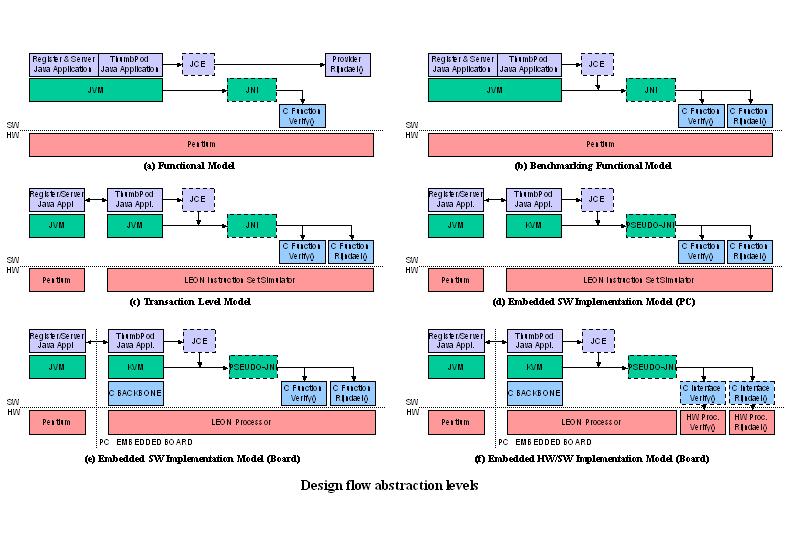
Los Angeles - UCLA